From new startups using IoT technology to disrupt entire industries to new wearable devices popping up, smart devices have been on the frontlines of innovation for quite a few years.
Over the past 15 years or so, a variety of appliances, machines, and traditionally non-smart hardware have been upgraded with sensors and software to enable them to exchange data over an internet connection.
The resulting devices have proven to be huge time-savers in people’s everyday lives, not to mention incredibly more efficient than traditional machines. So it is no wonder that analysts estimate there will be more than 75 billion IoT connected devices in use by 2025, a nearly threefold increase from 2019 figures.
As more interconnected devices help our farmers manage crops more efficiently, improve our manufacturing operations, and even make our homes more efficient, it’s time to take an in-depth look at their implications for the privacy and safety of our data.
What Are IoT Devices?
The Internet of Things, or IoT for short, refers to all the devices, appliances, and machines that connect to the internet. Most “things” marketed with the word “smart” in front of them fall into this category.
Examples include your smartphone and smartwatch, but also smart home appliances like thermostats, vacuums, security systems, and voice-operated assistants that can be programmed and controlled remotely.
The main advantage of IoT devices, and one of the main reasons they have become so ubiquitous, is that they allow people to automate a variety of daily tasks that are tedious and time-consuming—like vacuuming or doing laundry.
They also offer greater convenience than their traditional counterparts. As an example, while home music systems have been around for decades, smart speakers double as voice-enabled assistants that can set reminders, plan grocery lists, tell you the weather, and even control other smart devices in your home.
On the other hand, because smart devices need to be connected to the internet to function, they also create new risks for the security of your network.
IoT Devices Create New Security Risks
Take a look back at the last couple of years and consider that the COVID-19 pandemic caused a rapid acceleration in the rate of adoption of new technology. That, coupled with the sudden widespread shift to distributed workplaces, caused a significant surge in online threats, averaging at over 4,000 cyberattacks every day.
Also consider that large companies with properly structured cybersecurity architectures, like T-Mobile and the Colonial Pipeline, have fallen victim to shocking ransomware attacks.
So imagine for a second the security implications of introducing a large number of interconnected devices into the market with very basic cybersecurity systems built-in.
Each new IoT device becomes a new endpoint in the network, meaning it needs to be protected and monitor just like every other piece of internet-enabled technology, like laptops and smartphones. Because of this, the need for skilled cybersecurity professionals is skyrocketing to try and counteract the countless threats our digital world is facing.
You might think that hackers wouldn’t be particularly interested in breaking into your smart thermostat or lightbulbs. You’d be wrong. Any IoT device can give malicious actors a foothold into your network, which can subsequently be exploited to gain access to all other devices that connect to your wifi.
Protect Our Digital World by Learning Cybersecurity
The IT security sector has been outpacing many others in terms of job demand and the growing presence of IoT devices has made the need for skilled cybersecurity professionals even more critical.
If monitoring online systems for cyberattacks, securing networks from intrusions, and staying one step ahead of hackers sounds like a career you’d be interested in, there’s never been a better time to join the cybersecurity industry!
The University of Wisconsin—Madison offers a Cybersecurity Bootcamp that can help you gain the in-demand skills you need to succeed in this skyrocketing field.
Here’s how the bootcamp works: all classes take place live and online, and are led by cybersecurity experts, two sessions on weeknights, and one on Saturdays. The entire bootcamp is a total of 400 hours of hands-on cybersecurity instruction and takes about 10 months to complete.
You will learn from industry-leading, cybersecurity professionals who bring their experience directly into the classroom. You will practice new skills through hands-on simulations and cyber labs that mimic real-world cybersecurity scenarios. Plus, the UW—Madison Cybersecurity Bootcamp offers a dedicated career services department that can guide you along your cybersecurity journey.

Smart Devices Depend on the Internet
Without a reliable internet connection, smart devices aren’t able to transfer data and therefore cannot operate properly.
In case of a power outage, server problems, or any other issues that interrupt your internet connection, IoT devices will not work or be available for monitoring if you’re away. While the vast majority of smart home appliances, like refrigerators and washing machines, can also be operated manually, things like sensors and cameras feeding into your security system might fail altogether.
While the consequences of a failing internet connection are not likely to be extremely dire at the personal level, enterprises that rely on IoT tech for the normal functioning of their operations might be forced to suspend business altogether until the connection is restored.
IoT for Enterprises
Smart devices have become a vital resource for businesses across many different industries, especially in automating processes that used to be burdensome and making monitoring and maintenance much easier.
Fleet managers can use IoT devices to easily track individual shipments and even diagnose mechanical issues. Manufacturers can employ smart machines that help controlling quality standards and production times. Ranchers and farmers are able to use drones to survey remote agricultural terrains and monitor herds. Facilities managers can employ interconnected cameras and sensors to oversee the security of warehouses and offices with much greater ease than ever before.
IoT automations enable enterprises to save significant amounts of time and money, so it is no surprise that analysts believe the compound annual growth rate (CAGR) for IoT spending will reach 26.7% between 2022 and 2025.
Smart devices have found their way into every sector of our economy, playing an important role in the creation of what is now called Industry 4.0—a term that indicates the evolution of businesses, and especially manufacturing, through the integration of digital technologies like robotics, AI, cloud computing, and of course the Internet of Things.
Cybersecurity Risks for Smart Devices
While every single machine that connects to the internet runs the risk of being compromised in a security incident, smart devices are more susceptible to cyberattacks when compared to laptops and smartphones.
This is due, in part, to the fact that most IoT devices have less storage and processing power than computers, and that makes it difficult to protect them with anti-virus, firewalls, and other widespread security applications.
Another big factor that raises the risk profile of smart devices is simple human error. It is not always clear how new devices share consumers’ information with third parties, or what data they even require access to.
Uncovering this type of information can be a complicated process, and choosing the right settings to protect your privacy is often difficult. Because of this, most people don’t take the time to understand the nuances of what permissions their personal devices should have.
Some devices might be set up to share your information with third parties, while some others will not function properly unless you grant them unrestricted access. Enabling data sharing and other functionalities on your wearables and smartphones could create easy access points for hackers to steal your data.
No reason to despair, though, because there are many things you can do, on a personal level, to protect your privacy.
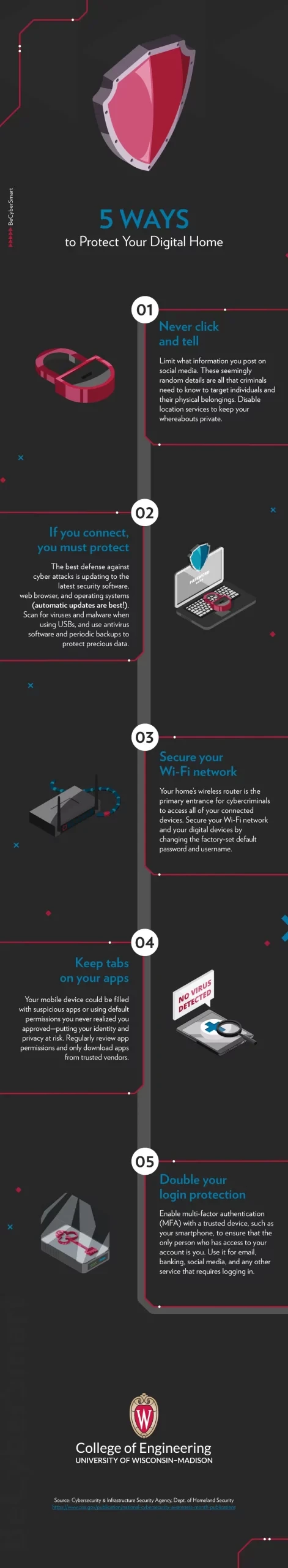
For tips on how to protect your smart devices, here’s a handy and easy-to-share infographic guide: